Vobo’s Security & Privacy Commitment
At Vobo, we believe that your data is your property—always.
When you use our platform, every conversation, file, image, and record you share remains under your full control. We never sell your data, we never mine it for advertising, and we never feed it into AI models. Your private community is exactly that—private.
Our Privacy Principles:
- Client-Owned Data – All information stored on Vobo belongs solely to you and your organization.
- No Data Resale or Monetization – We do not sell, rent, or trade your information to any third party.
- No AI Training on Your Content – Your data is never reviewed or processed for use in our AI systems.
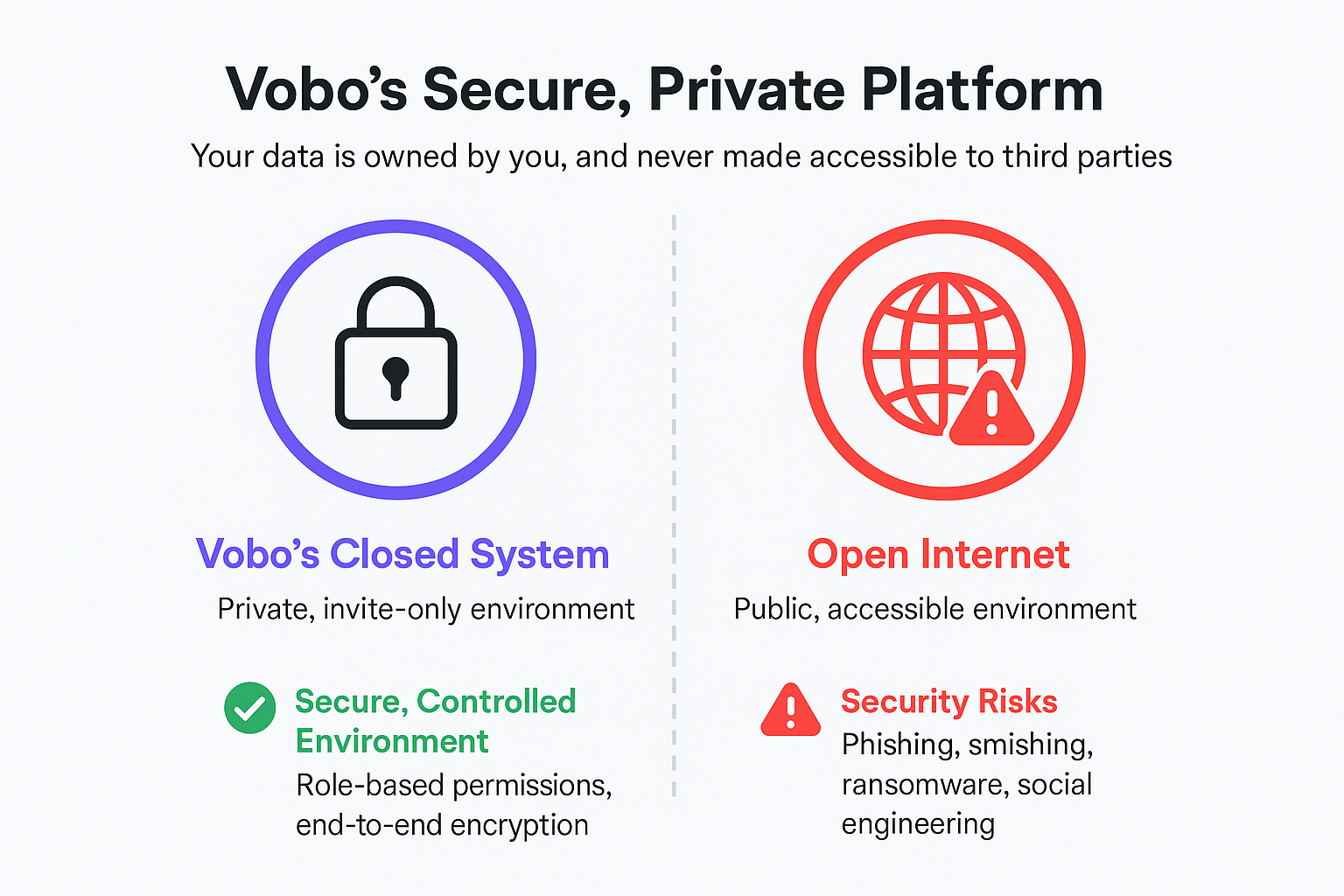
- Secure, Controlled Access – Role-based permissions ensure only authorized members can see or interact with your information.
- End-to-End Protection – All messages, files, and content are encrypted in transit and at rest.
Why Privacy Matters: Risks of Open Internet Platforms
Many public or “free” platforms rely on advertising models that depend on data harvesting. This creates an environment where your information may be tracked, analyzed, and monetized, often without your full understanding. Worse, open networks are frequent targets for cybercriminals, creating multiple security threats:
- Phishing – Fraudulent emails or messages tricking users into revealing sensitive information.
- Smishing – SMS-based phishing attacks that impersonate trusted contacts or services.
- Ransomware – Malicious software that encrypts your files and demands payment for release.
- Social Engineering – Psychological manipulation to gain unauthorized access to accounts or systems.
- AI-Enhanced Threats – Cybercriminals are now using advanced AI to create more convincing scams, automate attacks, and mimic trusted individuals with alarming accuracy.
Vobo’s Safe, Private Network
Vobo is built to counter these threats by keeping your community in a closed, invite-only environment, completely isolated from the open web. By removing exposure to public search engines, anonymous accounts, and uncontrolled data flows, we drastically reduce the risk of intrusion and exploitation.